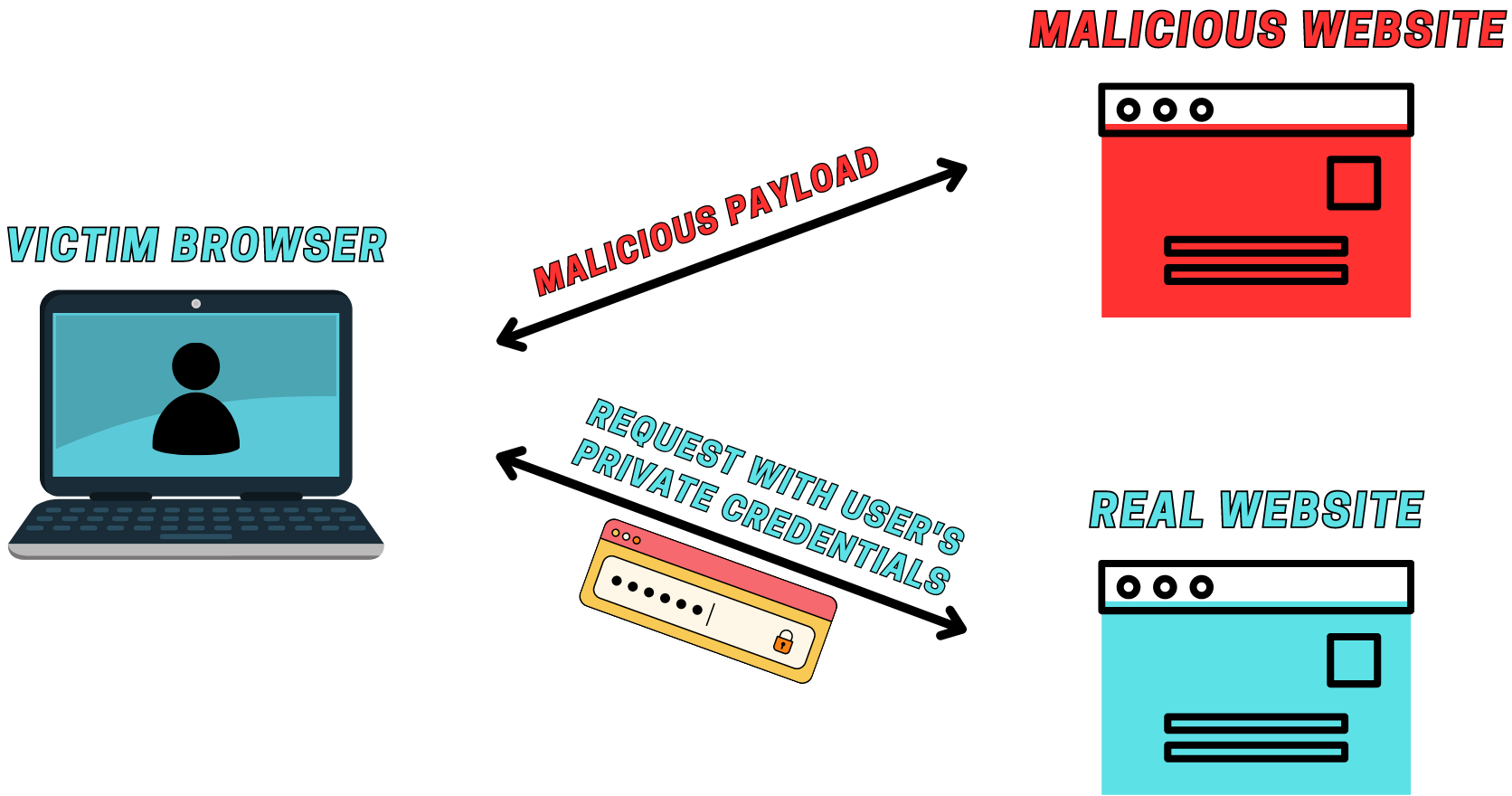
Testing for CSRF with Burp Suite
Testing for Cross-Site Request Forgery (CSRF) is a critical aspect of web application security. Burp Suite offers a robust set of tools to identify and exploit CSRF vulnerabilities. Here's a step-by-step guide to performing CSRF testing using Burp Suite:
Before you continue with the steps, make sure you've configured and setup Burp Suite. If you haven't refer to this page to set up Burp Suite.
For this tutorial, I am using a demo open-source website that is vulnerable to CSRF attacks. The link is here if you want to recreate the steps.
Step 1: Identify the Target
Start by identifying the specific request within the target web application that you want to test for CSRF. This could be a form submission, a login request, or any other action that requires user authentication. Go to Burp Suite's Proxy tab, switch the "intercept" tab off, and open the web application in your configured browser.

Step 2: Send Request to Burp Intruder
Enter the credentials in the fields you want to alter.

Then go back to Burp Suite and switch the "Intercept is off" button to "Intercept is On"

Now follow through with the request. For my web application I am testing, I would click "Login" for example.
Once the target request is captured in the Burp Proxy history, right-click on it and select "Send to Intruder." This will allow you to analyze the request and manipulate its parameters using Burp Intruder, a powerful tool for automating customized attacks.
Step 3: Analyze the Request
In this step, you'll need to analyze the request to identify all the parameters that are included in the CSRF token. You can do this by sending the request to the Repeater tool:
Right-click > Send to Repeater
Within the Repeater, you can view and modify the request, allowing you to understand how the CSRF token is constructed and how it might be exploited.
Step 4: Generate CSRF PoC
Once you've analyzed the request, you can use Burp Suite's built-in "Generate CSRF PoC" (Proof of Concept) feature. This will create a sample HTML form that simulates the malicious request an attacker might use to exploit the CSRF vulnerability. Simply right-click on the request and select "Generate CSRF PoC" to create the attack code.
Right-click > Engagement Tools > Generate CSRF PoC
Step 5: Test the PoC
After generating the proof-of-concept, test it in a browser where the user is authenticated. This will help you verify whether the CSRF vulnerability exists and how it behaves. Make sure to observe the response and any changes on the target site to understand the impact of the vulnerability.
Additional Resources
For more detailed information, advanced techniques, and continuous learning, refer to the official Burp Suite documentation on CSRF testing.
Here is also a great simple Youtube tutorial on how to perform CSRF with Burp Suite for free.