
What is Burp Suite
Burp Suite is a popular penetration testing tool used for security testing of web applications. It is designed to be used by security professionals to aid in the process of web application assessments. Features include intercepting proxy, spider, intruder, repeater, sequencer, decoder, and comparer.
Burp Suite for XSS Attacks
Burp Suite can be used to perform XSS attacks:
- Intercepting Proxy: Allows the tester to intercept, inspect, and modify the raw traffic passing between the browser and the web server.
- Spider: Used for mapping the application content by following links to discover content and functionality.
- Intruder: Used for performing automated attacks on web applications. It can be used to craft malicious inputs to perform XSS attacks.
XSS using Burp Suite
There are several techniques that attackers use to exploit XSS vulnerabilities using Burp Suite:
HTML Injection
HTML Injection involves injecting malicious HTML code into a website, which is then executed by the victim's browser. Here's how you can use Burp Suite's tools for this technique:
- Ensure that Burp is correctly configured with your browser. Refer to our Burp Suite for Application Testing page if it is not configured.
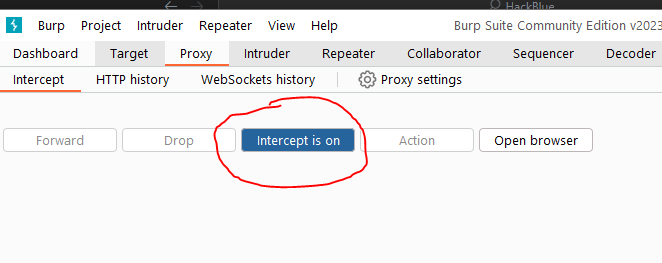
- With intercept turned on in the Proxy "Intercept" tab, visit the web application you are testing.
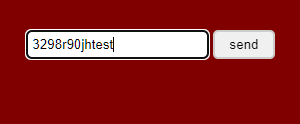
- Enter an arbitrary string that doesn't appear within the application and contains only alphabetic characters.
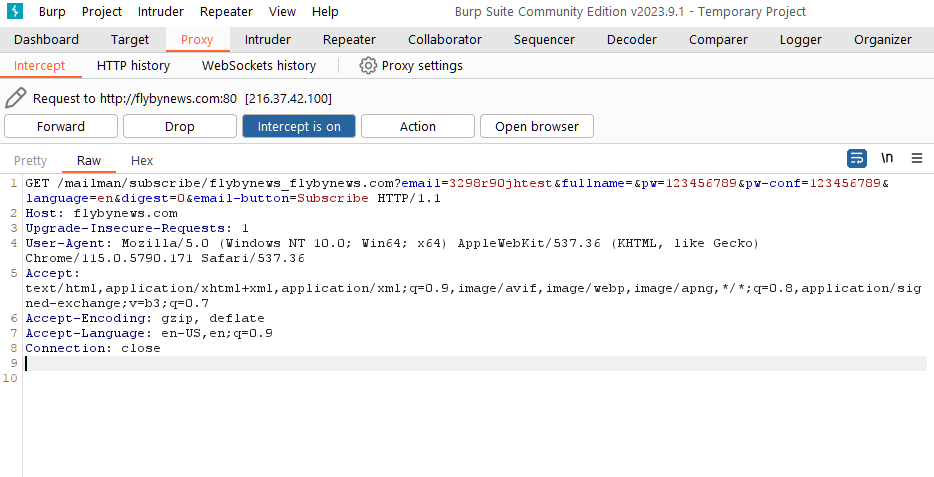
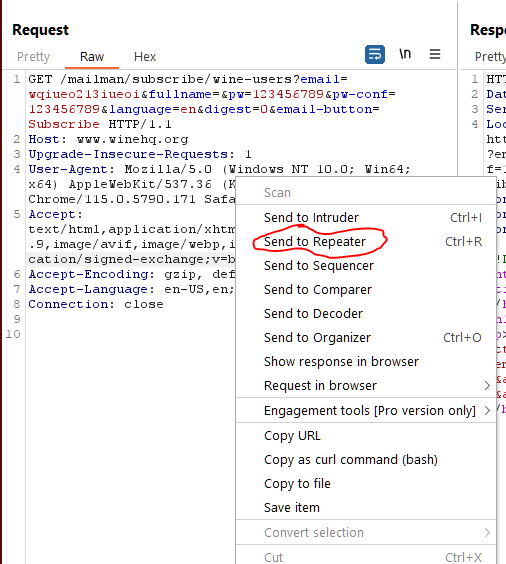
- The request will be captured by Burp. Right-click on the request and select "Send to Repeater".
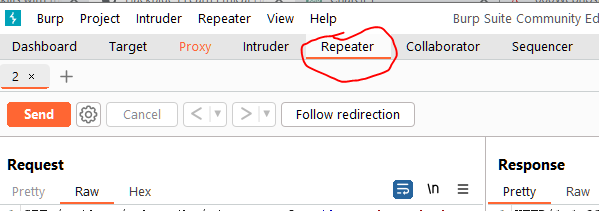
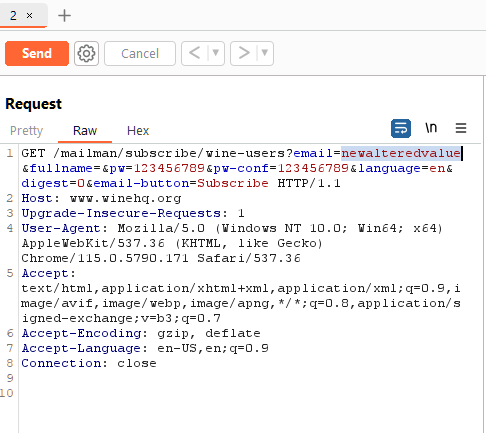
- In the Repeater tab, input various XSS payloads into the input field of the web application.
- Submit this string as every parameter to every page, targeting only one parameter at a time.
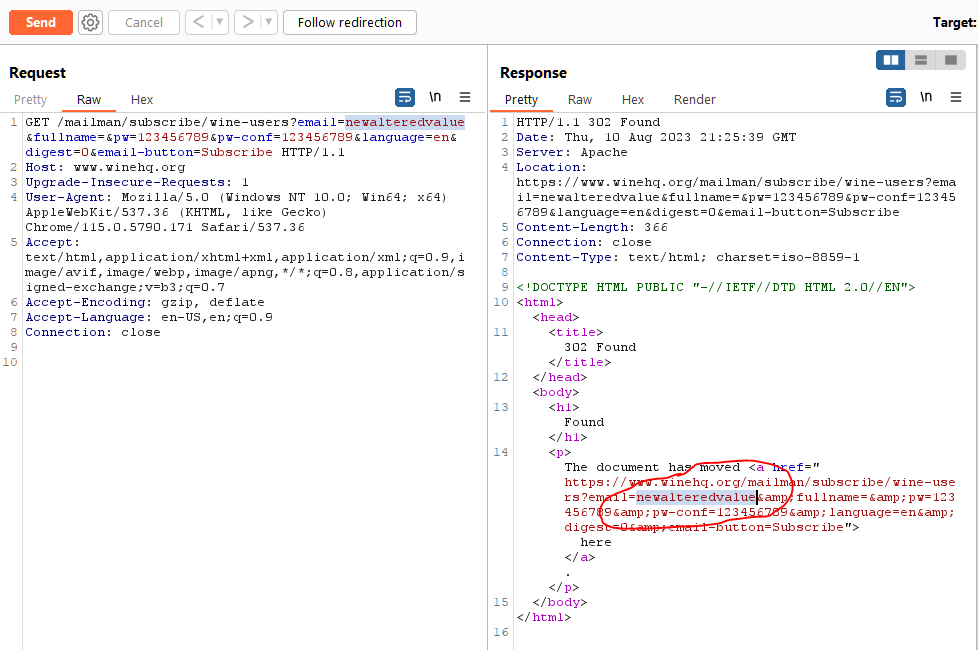
- Review the HTML source to identify the location(s) where your unique string is being reflected.
- Introduce JavaScript without causing an error and work around any defensive filters.
- Test your exploit by submitting it to the application. If your crafted string is returned unmodified, the application is vulnerable.
JavaScript Injection
JavaScript Injection involves injecting malicious JavaScript code into a website, which is then executed by the victim's browser. This can lead to the modification of page content or script execution from attacker-controlled sites. Using Burp Suite's Intruder tool, you can automate the process of injecting malicious JavaScript payloads into different parts of the web application to identify potential vulnerabilities.
Learn more about using Burp Intruder for Javascript injections and customizing attacks against Web Applications
Document.cookie
Now given the basics of using Burp Suite to intercept requests and customize XSS attacks, try to exploit cross-site scripting to steal cookies from a web application. The Document.cookie technique involves capturing the victim's cookies, which may contain sensitive information such as login credentials.
Click here to take on a lab where your goal is to exploit XSS to steal cookies
Solution VideoPreventing XSS with Burp Suite
Burp Suite can also be used to prevent XSS attacks. Its Scanner tool can be used to automatically find and report XSS vulnerabilities. The reported issues provide detailed information about the vulnerabilities, including the location, the payload that was used to find the vulnerability, and remediation advice.