Web Application Hacking
Burp Suite is a powerful web application security testing tool. It is widely used by ethical hackers and penetration testers to identify vulnerabilities in web applications. The tool is equipped with a variety of features that allow for web traffic interception, manipulation, and replaying of requests, among other things. For this Burpsuite tutorial we will be utilizing "Burpsuite Community", which is the free version of the tool.
Installation of Burp Suite
Burp Suite is a renowned web application vulnerability scanner and penetration testing tool. It's available in community, professional, and enterprise editions, with the community edition being free with limited features. Here's how you can install Burp Suite on Windows and Linux (Ubuntu).
Windows Installation
Follow these steps to install Burp Suite on Windows:
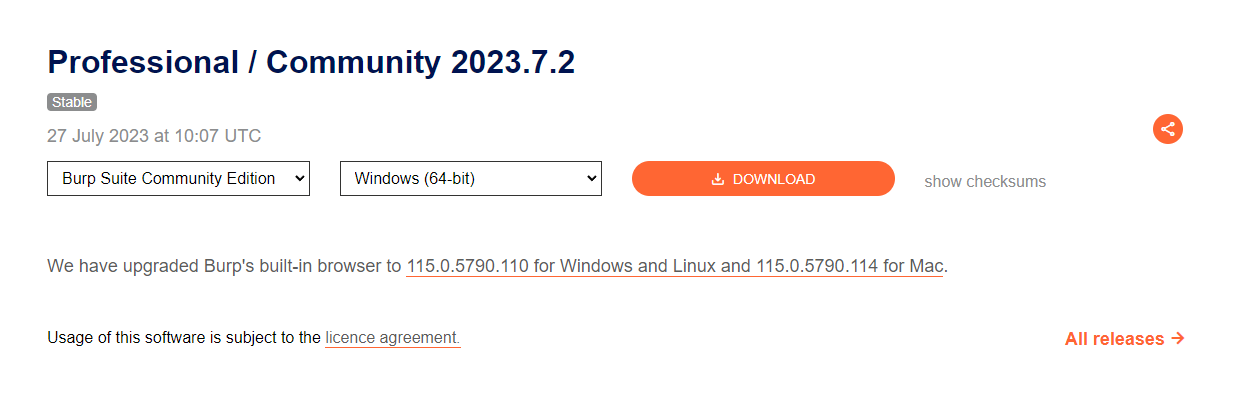
- Visit the download page for Community Burp Suite
- Choose Burp Suite Community Edition for Windows (64-bit) and click on the download button.
- Run the downloaded executable file.
- Follow the Installation Wizard, selecting the desired installation location and Start menu folder.
- Click on Finish after the installation process is complete.
- Run the software, accept the terms and conditions, choose a temporary project, and click Next.
- Click on "Use Burp Defaults," and the new project window will appear.
Linux (Ubuntu) Installation
Follow these steps to install Burp Suite on Ubuntu:
- Open your system's default browser.
- Visit the Burp Suite Download page, select Linux, and save the installation script.
- Open command terminal (Ctrl+Alt+T).
- Switch to the Downloads directory and make the downloaded file executable using
chmod +x filename
"filename" should look something like "burpsuite_community_linux_v2023_7_2.sh" - Run the file using
sudo ./filename
- Follow the GUI installation wizard, selecting the desired installation directory and other preferences.
- Start Burp Suite from the command line or GUI using
BurpSuiteCommunity
or by clicking on the Burp icon. - Create a temporary project and start using the software.
To update or uninstall Burp Suite, follow the instructions provided in the installation folder.
More details on Ubuntu installation
Official Documentation for Downloading Burp Suite
Setting Up Burp Suite
Before you start using Burp Suite, you need to configure your browser to work with it. This involves setting up a proxy in your browser settings to route traffic through Burp Suite. Below are the step-by-step instructions for configuring Burp Suite with both Chrome and Firefox browsers.
Chrome Configuration
Follow these steps to configure Burp Suite with Chrome:
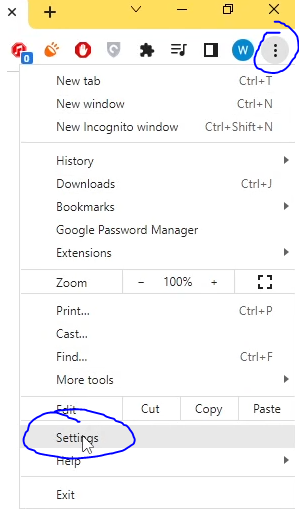
- Open Chrome and go to the settings page.
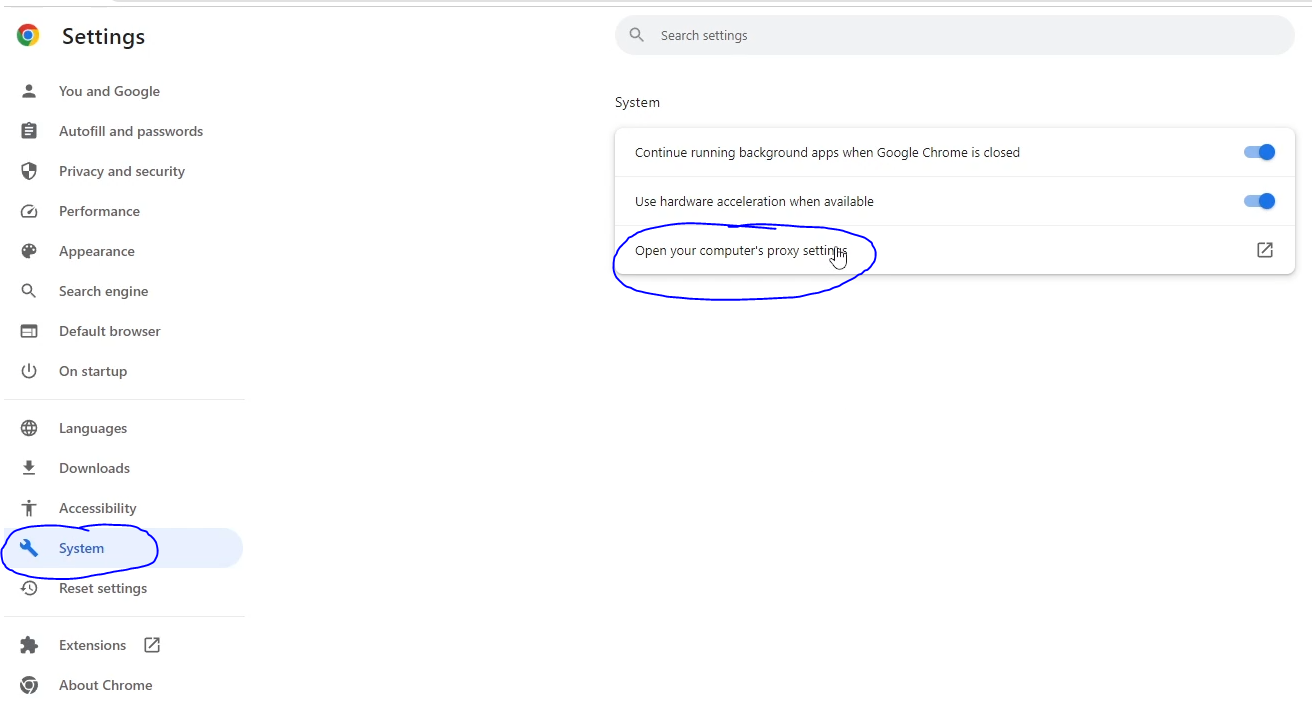
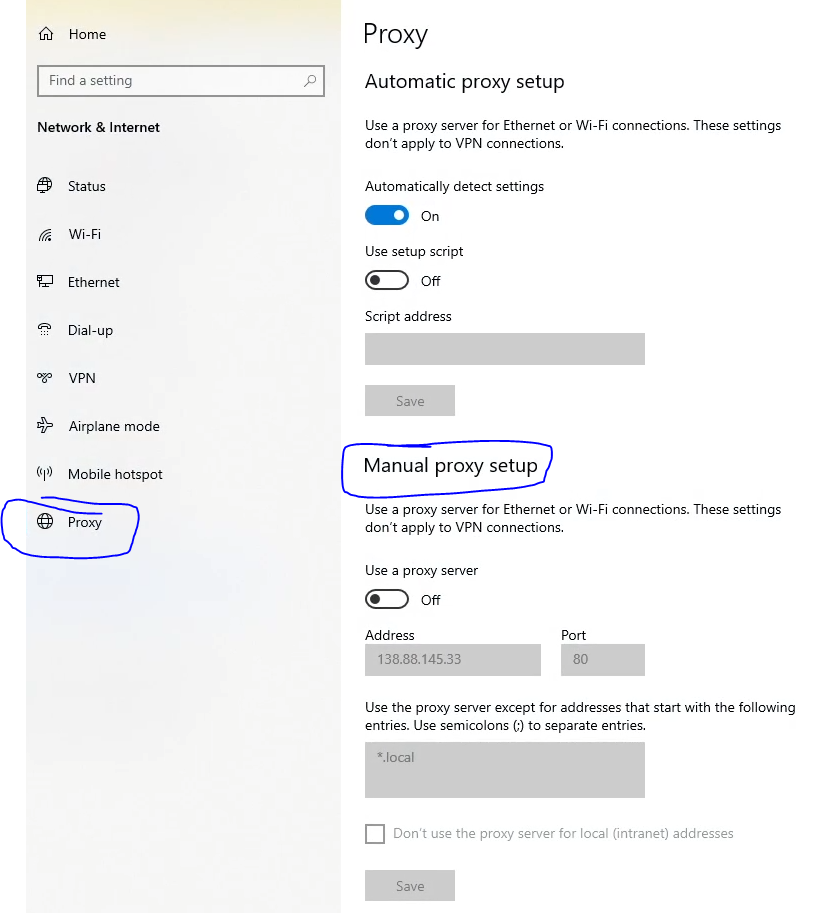
- Under 'System', click on 'Open your computer's proxy settings'.
- In the 'Proxy' settings window, find the 'Manual proxy setup' settings.
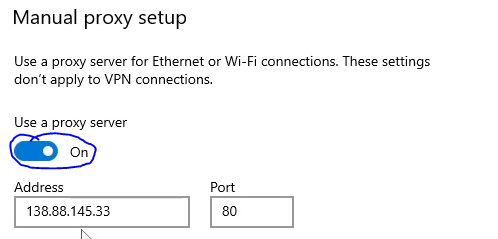
- Toggle the "on" option for 'Use a proxy server'.
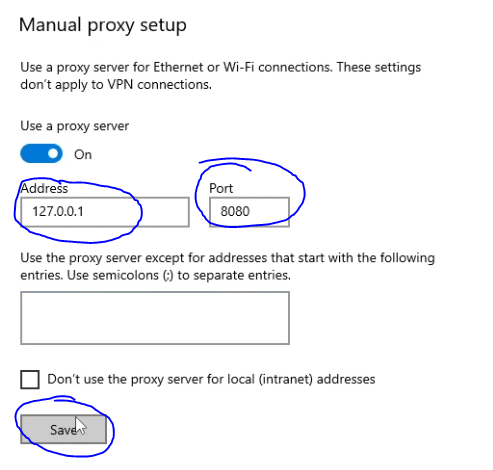
- Enter '127.0.0.1' in the 'Address' field and '8080' in the 'Port' field.
- Click 'OK' to save the settings.
Now, Chrome is configured to use Burp Suite as its proxy.
Firefox Configuration
Follow these steps to configure Burp Suite with Firefox:
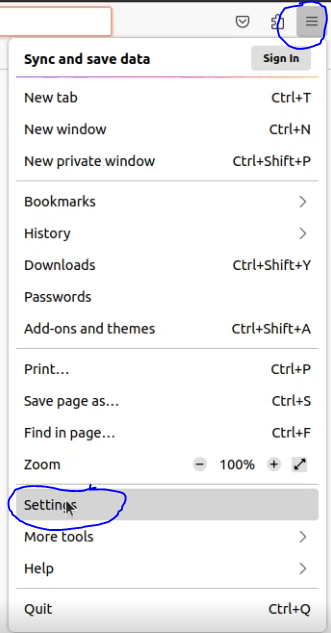
- Open Firefox and click on the menu button (3 horizontal lines) in the top right corner, and select 'Settings'.
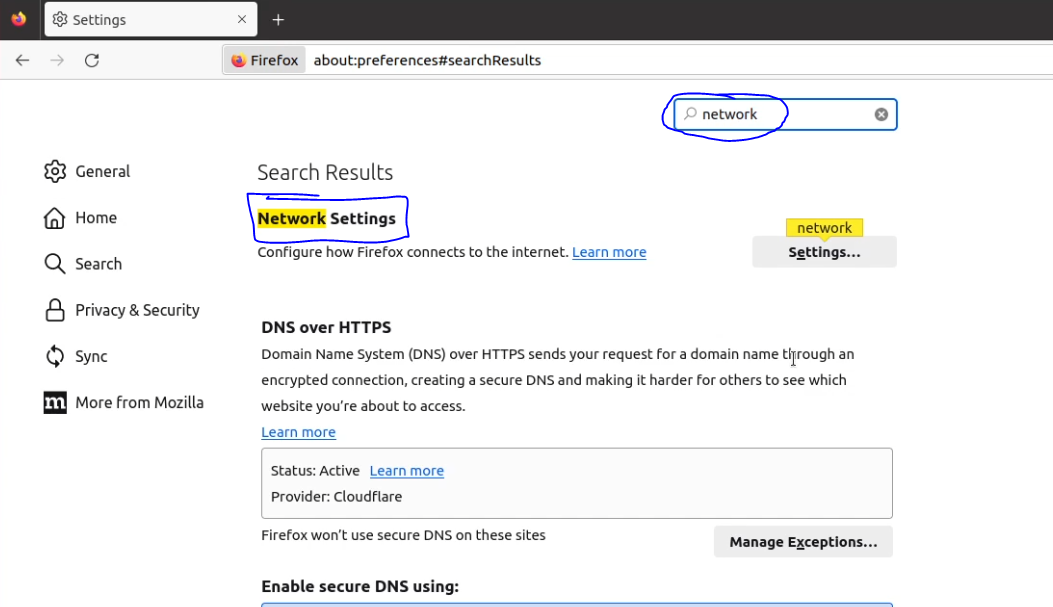
- Search for "Network" in the settings search bar
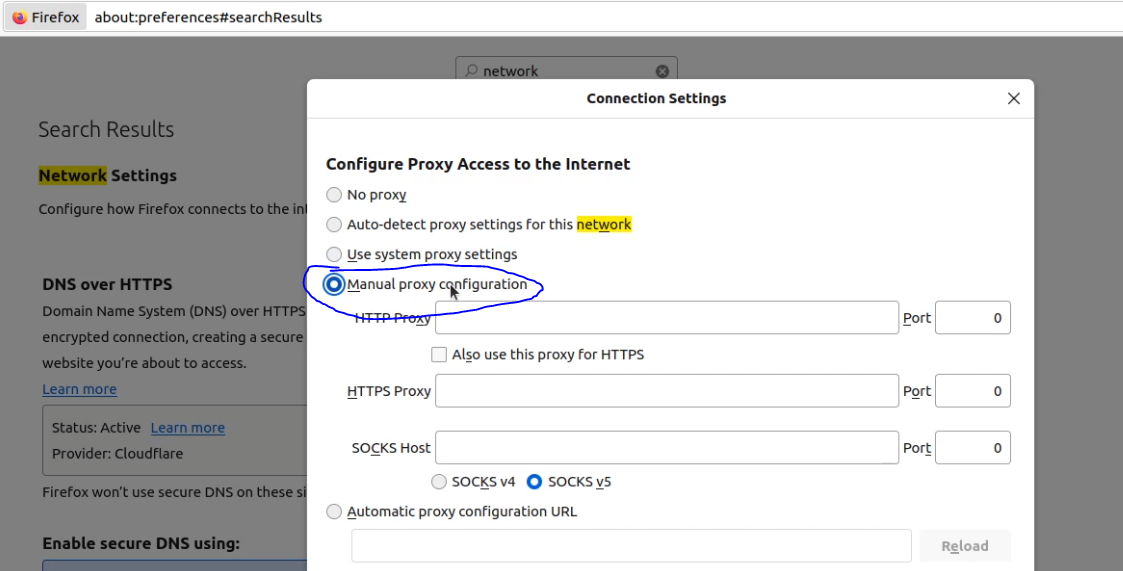
- Select 'Manual proxy configuration'.
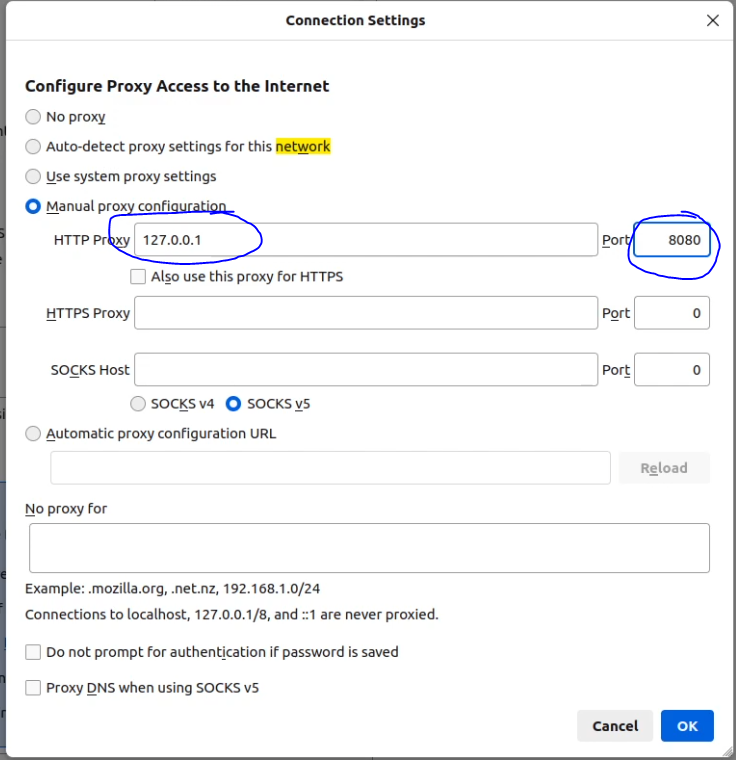
- Enter '127.0.0.1' in the 'HTTP Proxy' field and '8080' in the 'Port' field.
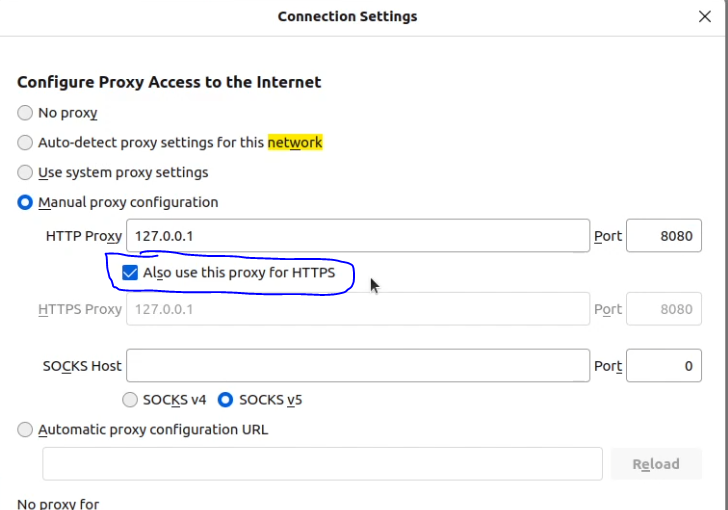
- Check the box for 'Use this proxy server for all protocols'.
- Click 'OK' to save the settings.
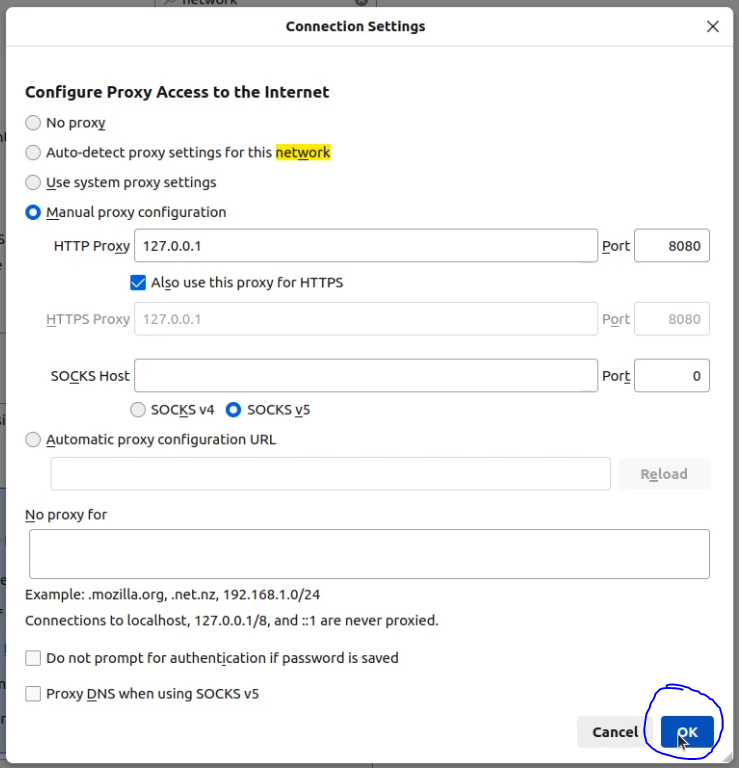
Now, Firefox is configured to use Burp Suite as its proxy.
Intercepting HTTP Requests
Once the setup is complete, you can start intercepting requests.
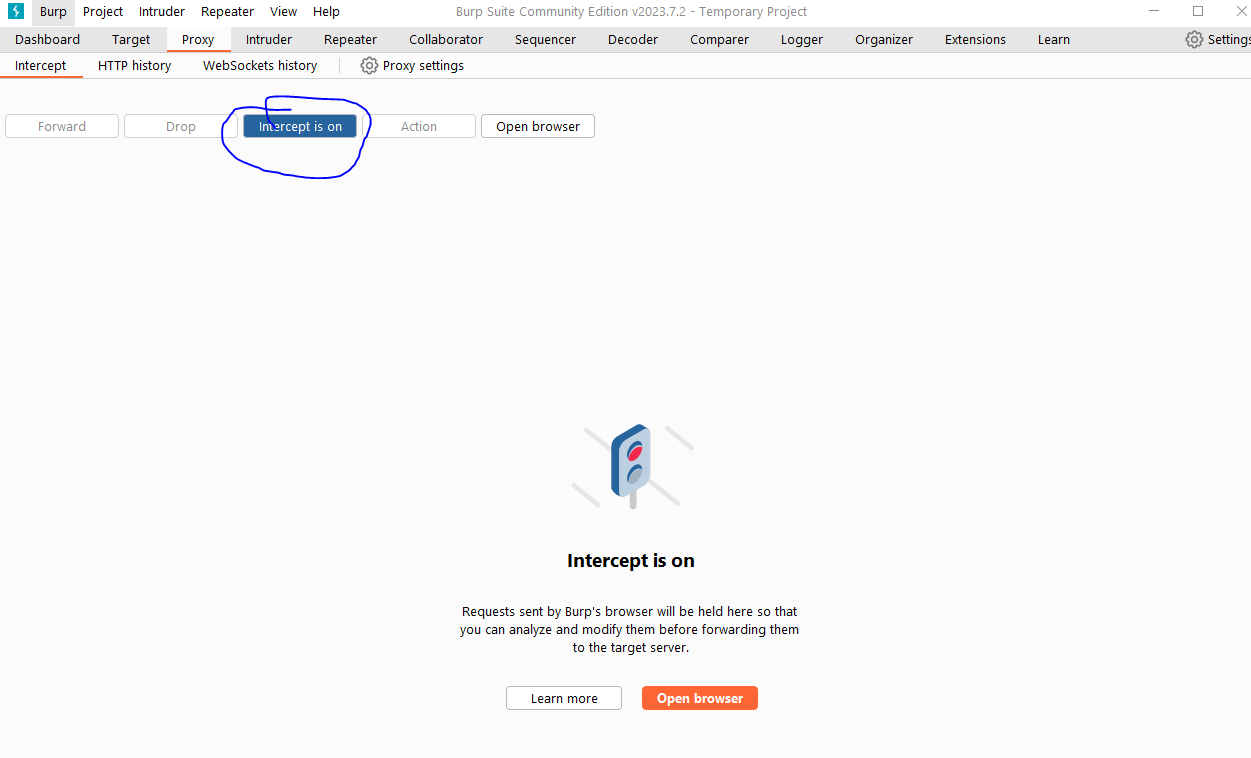
- To do this, navigate to the 'Proxy' tab and ensure that the 'Intercept is on' button is enabled. Now, when you navigate to a website in your browser, the requests will be captured in Burp Suite.
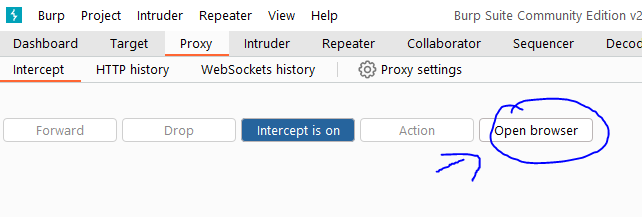
- Alternative: If your browser isn't configured, you can also click on the "Open browser" button to open an automatically configured browser ready to intercept requests.
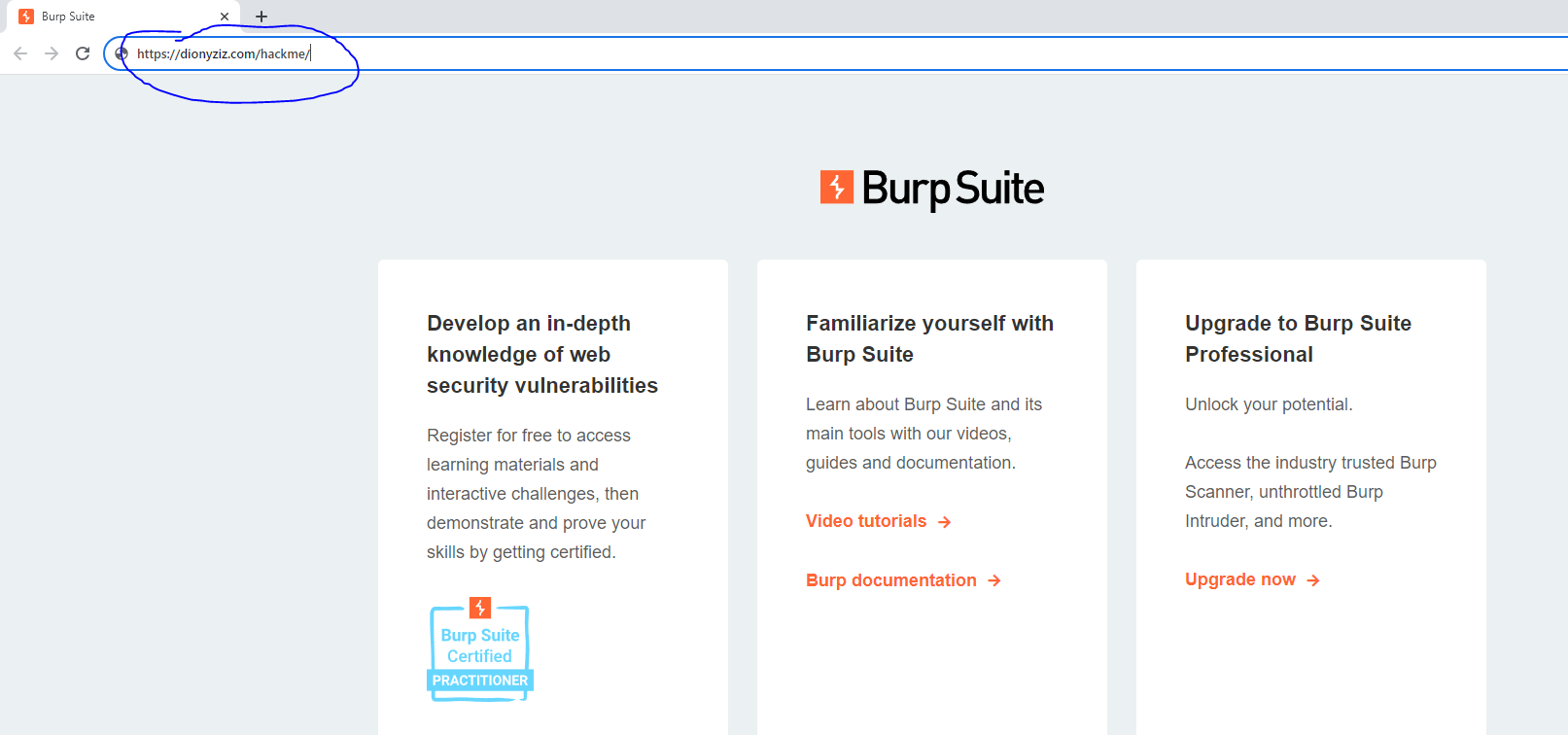
- Type in the URL of the web application you want to test (Note - dionyziz.com/hackme is a public website that gives everyone permission to hack)
- As you can see, the request to the website has been intercepted
- You can also explore the HTTP history tag to see the history of HTTP requests
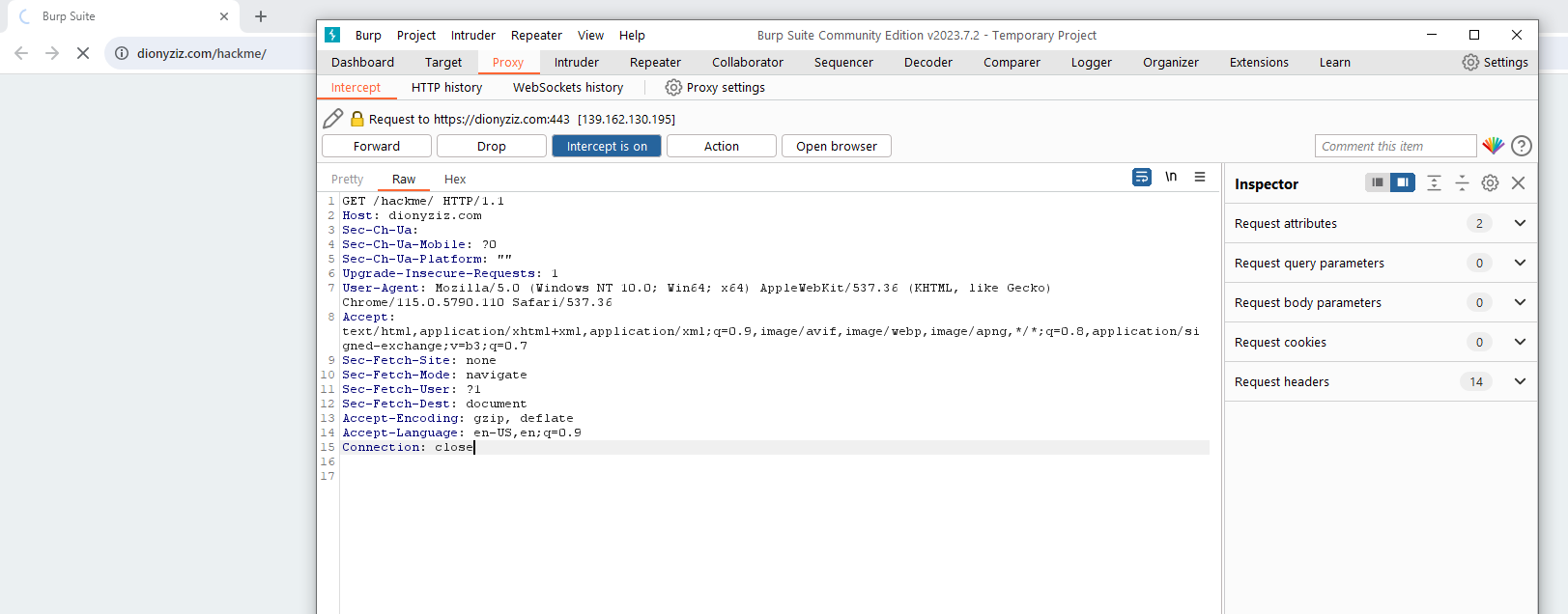
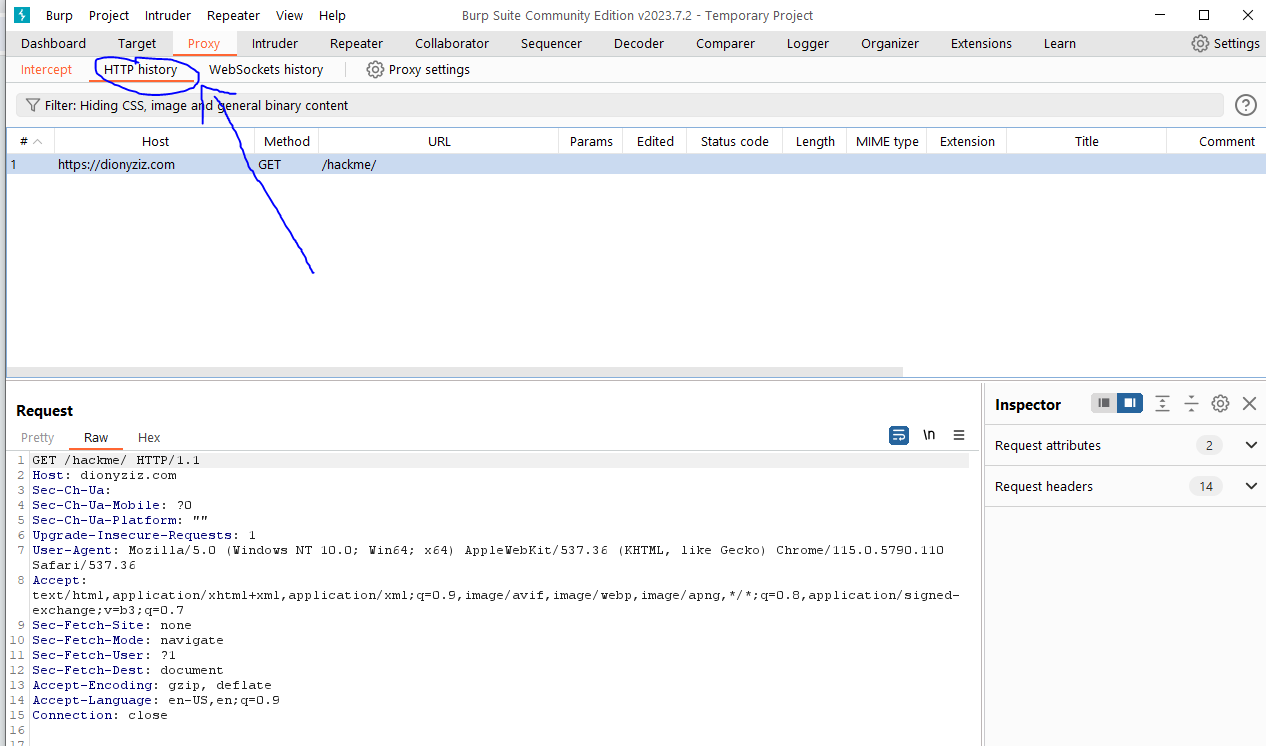
Analyzing Requests
With the intercepted request in Burp Suite, you can analyze the details of the request. This includes the headers, parameters, and cookies. Understanding these details is crucial for identifying potential vulnerabilities.
Conclusion
Burp Suite is a comprehensive tool for web application security testing. With its various features, it allows penetration testers to effectively identify and exploit vulnerabilities. However, it's important to remember that automated tools like Burp Suite should be used in conjunction with manual testing techniques for the best results. Under the Web Hacking Section more in-depth hacks involving Burp Suite will be covered.