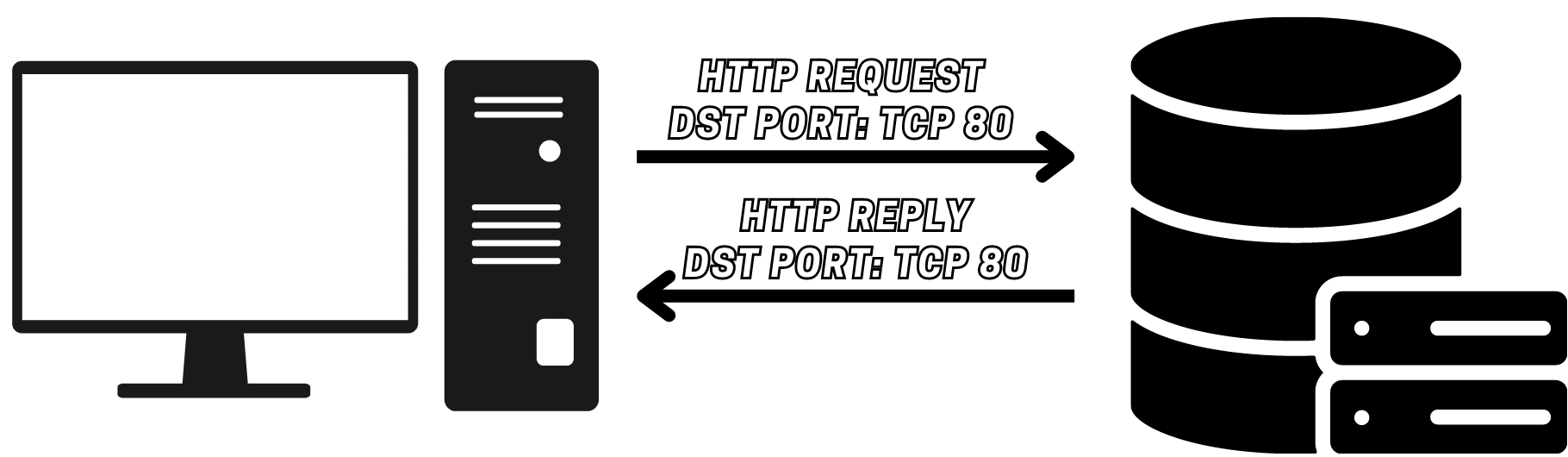
What is a Port?
A port is a logical endpoint in a network connection, used by protocols to organize data traffic. Ports allow different applications on the same device to use network resources simultaneously. In the context of cybersecurity, understanding ports is crucial for network scanning, vulnerability assessment, and intrusion detection. Ports are categorized into three main ranges: well-known ports (0-1023), registered ports (1024-49151), and dynamic or private ports (49152-65535). Each range serves specific purposes and follows certain conventions.
Common Ports
Some of the most commonly used ports in networking and their associated protocols include:
- HTTP (Port 80) - Used for unencrypted web traffic, often targeted for man-in-the-middle attacks.
- HTTPS (Port 443) - Used for secure web traffic, encrypting data to prevent eavesdropping.
- FTP (Ports 20/21) - Used for file transfer, with potential vulnerabilities if not configured properly.
- SSH (Port 22) - Used for secure remote access, a critical component in secure network management.
- SMTP (Port 25) - Used for email sending, often exploited for spamming and phishing attacks.
What is TCP and UDP?
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) are two of the main transport layer protocols used in network communication. TCP is connection-oriented, ensuring data integrity and delivery, while UDP is connectionless, prioritizing speed over reliability. Understanding these protocols is essential for network analysis, penetration testing, and secure communication design. TCP is often used for applications that require reliability, such as web browsing and email, while UDP is used for real-time services like video streaming and online gaming.
Port Scanning
Port scanning is a technique used by ethical hackers to discover open ports on a target system. It helps in identifying vulnerabilities and potential entry points for attacks. Tools like Nmap are commonly used for port scanning, and understanding how to interpret the results is vital for network security assessment. Different scanning techniques, such as SYN scan, ACK scan, and Stealth scan, provide various insights and can evade detection by intrusion prevention systems.
Protocols in Security
Various security protocols are implemented to ensure secure communication over a network. Some common security protocols include:
- SSL/TLS - Used for secure web communication, protecting data integrity and confidentiality.
- IPsec - Used for secure VPN connections, encrypting data at the IP layer.
- SFTP - Secure file transfer protocol, providing encrypted file transfers.
- SSH - Secure shell for encrypted remote access, essential for secure system administration.
Best Practices for Port and Protocol Security
Proper management of ports and protocols is essential for maintaining a secure network environment. Best practices include:
- Regular Monitoring: Continuous monitoring of open ports and active services to detect unauthorized access.
- Firewall Configuration: Implementing proper firewall rules to control inbound and outbound traffic, blocking unnecessary ports.
- Using Secure Protocols: Opting for secure versions of protocols whenever possible, such as HTTPS over HTTP.
- Regular Patching: Keeping software and protocols up to date with the latest security patches to fix known vulnerabilities.
- Network Segmentation: Isolating different parts of the network to contain potential breaches and minimize risk.